Axidian presents a new version of Axidian Privilege. Axidian Privilege 2.5 offers enhanced access policy mechanisms, new features and improvements in the user and administrator interface, as well as additional connectors to target resources. Please see below for an overview of the new release.
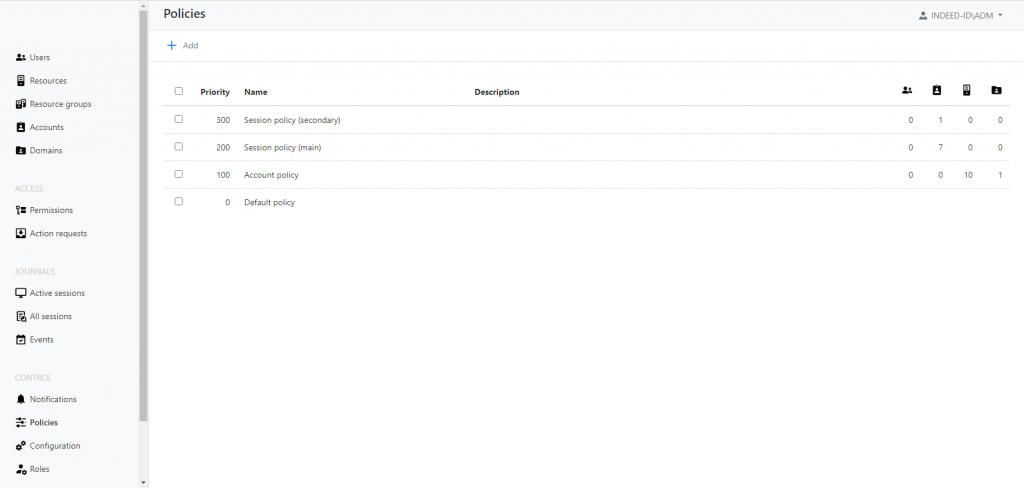
New access policy mechanism
Axidian Privilege relies on proprietary policies for customizing access settings for specific target resources and privileged accounts. But real-life applications and the growing number of scenarios dictate new requirements. We present a new, more flexible mechanism where restrictions to individual policy settings no longer apply, and policies can be assigned to all types of Axidian Privilege objects (resources, user accounts, domains, or users).
Now, your solution administrators have at their disposal a special kit that can generate unique settings for specific Axidian Privilege objects. The new version also includes a default policy for all operating Axidian Privilege parameters that can be applied to all objects. This will make the administrators’ job much easier if they do not require individual settings for different user groups or resources.
New connectors to target resources
Axidian Privilege 2.5 supports new types of user and service connections:
- Telnet – user connections intended for monitoring telnet sessions initiated via Axidian Privilege.
- Cisco – service connections for Cisco network equipment intended for monitoring user accounts in IOS XE.
- Inspur BMC – service connections intended for managing user accounts in the Inspur IPMI module.
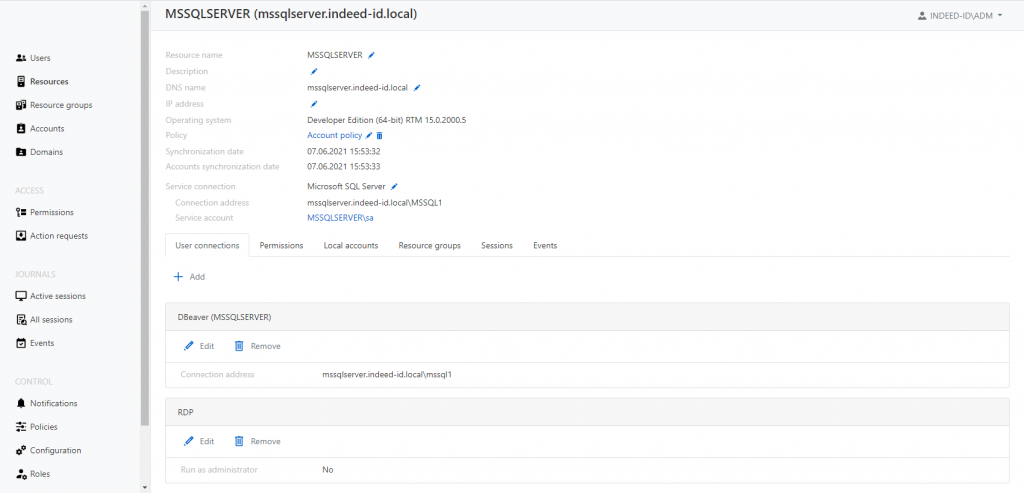
Multiple user connections to one resource
New features also apply to the resources being added to Axidian Privilege. The new version supports different types of connections to the same target resource. When assigning permissions, your PAM administrator can specify the connection methods that will be available to users.
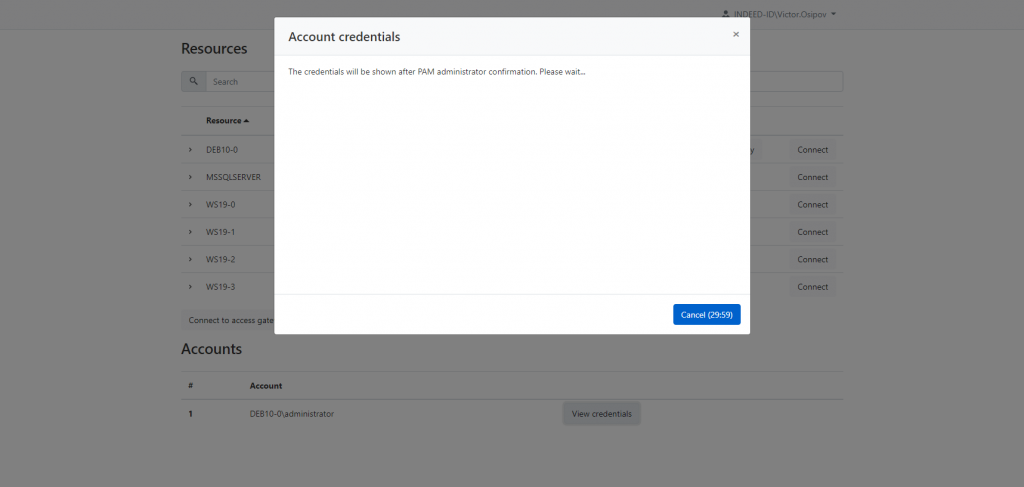
Passwords to privileged accounts can be viewed upon approval (confirmation) by Axidian Privilege administrator
Users who already had a chance to use the previous versions of Axidian Privilege must be familiar with the procedure that involves the approval (or confirmation) of all new privileged sessions by the administrator. In Axidian Privilege 2.5, the scope of operations requiring the administrator’s approval has been expanded. You can now make the Axidian Privilege administrator confirmation mandatory for all attempts to view privileged account passwords.
Passwords / SSH keys will be automatically reset upon session termination or stored password mismatch
Each new version of our software suite features essential improvements designed to ensure the security of your privileged user accounts and PAM servers. This release is no exception as it includes two important updates:
- All passwords / SSH keys of your privileged user accounts will be immediately reset after the session is terminated.
- All passwords / SSH keys will be reset whenever the system detects that the stored password differs from the actual privileged account password.
The new features can help you improve the rotation of your privileged authentication data and introduce one-time password (session key) authentication, with new credentials required for each new session.
Other updates
The new version of Axidian Privilege features a series of updates designed to improve privileged user / PAM administrator experience:
- In the user console you can get a connection string for the Axidian Privilege SSH Proxy server. All you need to do is click the Copy button, and the relevant SSH client invocation command will be saved in your clipboard.
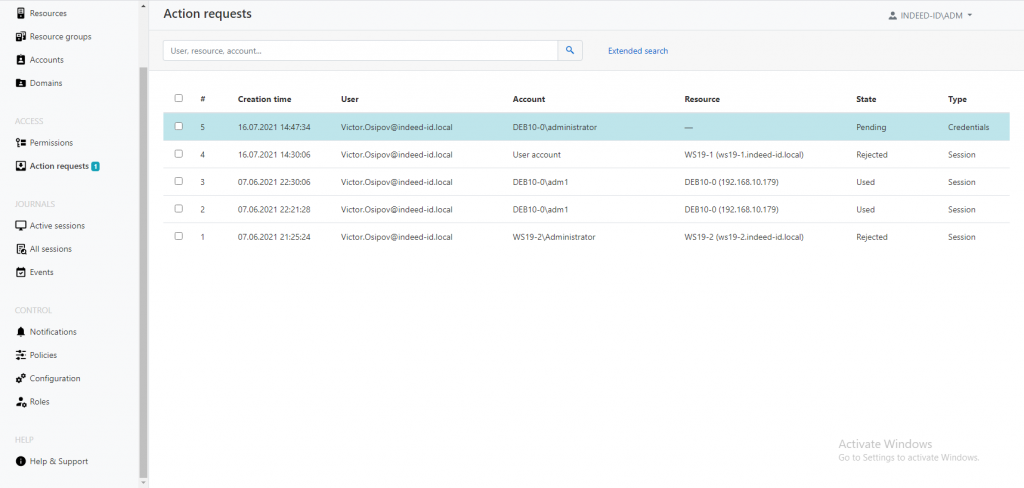
- The lines containing requests to initiate sessions or view passwords are now highlighted in color, making the system more user-friendly for Axidian Privilege administrators.
- Kiosk mode will be used for all HTTP(S) sessions launched via Axidian Privilege. This can help you strengthen the overall security levels for all thin-client connections to various target resources.
- The new release also features CEF and LEEF event formats for the Syslog server.
- Most tables in the Management Console now support data sorting.



